更新時間:2021-11-02 11:36:05 來源:動力節(jié)點 瀏覽893次
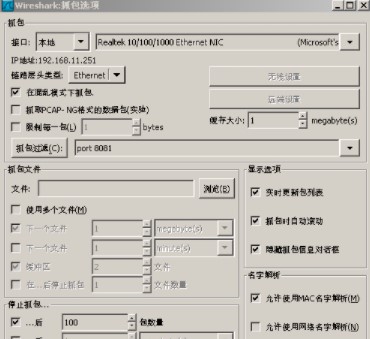
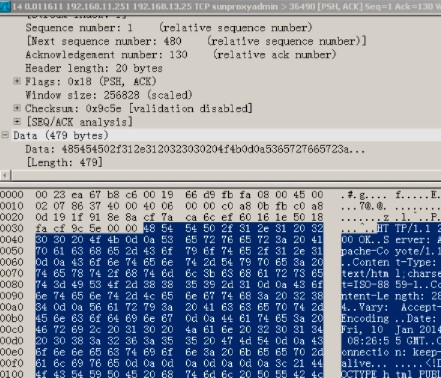
然后 就可以分析tcp的報文了
但是捕獲環(huán)回數(shù)據(jù)包不行,比如本地啟動了一個tomcat應用,用本地環(huán)回數(shù)據(jù)包捕獲就無法捕獲。
[root@paas-boss-db1 tcpdump-4.3.0]# ./tcpdump port 8080
tcpdump: verbose output suppressed, use -v or -vv for full protocol decode
listening on eth0, link-type EN10MB (Ethernet), capture size 65535 bytes
09:48:56.189411 IP PAAS-BOSS-DB1.webcache > 192.168.11.251.4506: Flags [F.], seq 3372045395, ack 4061102965, win 63, length 0
09:48:56.189511 IP PAAS-BOSS-DB1.webcache > 192.168.11.251.4503: Flags [F.], seq 3363610217, ack 766993567, win 88, length 0
09:48:56.190118 IP 192.168.11.251.4503 > PAAS-BOSS-DB1.webcache: Flags [.], ack 1, win 64240, length 0
09:48:56.190149 IP 192.168.11.251.4506 > PAAS-BOSS-DB1.webcache: Flags [.], ack 1, win 63997, length 0
09:48:56.190346 IP PAAS-BOSS-DB1.webcache > 192.168.11.251.4505: Flags [F.], seq 3364472081, ack 2651406034, win 71, length 0
09:48:56.190433 IP PAAS-BOSS-DB1.webcache > 192.168.11.251.4507: Flags [F.], seq 3368042724, ack 796427157, win 54, length 0
09:48:56.190532 IP 192.168.11.251.4506 > PAAS-BOSS-DB1.webcache: Flags [F.], seq 1, ack 1, win 63997, length 0
09:48:56.190543 IP PAAS-BOSS-DB1.webcache > 192.168.11.251.4506: Flags [.], ack 2, win 63, length 0
09:48:56.190608 IP 192.168.11.251.4507 > PAAS-BOSS-DB1.webcache: Flags [.], ack 1, win 64075, length 0
09:48:56.190620 IP 192.168.11.251.4505 > PAAS-BOSS-DB1.webcache: Flags [.], ack 1, win 64200, length 0
09:48:56.191317 IP 192.168.11.251.4505 > PAAS-BOSS-DB1.webcache: Flags [F.], seq 1, ack 1, win 64200, length 0
09:48:56.191322 IP PAAS-BOSS-DB1.webcache > 192.168.11.251.4505: Flags [.], ack 2, win 71, length 0
09:48:56.191450 IP 192.168.11.251.4507 > PAAS-BOSS-DB1.webcache: Flags [F.], seq 1, ack 1, win 64075, length 0
09:48:56.191456 IP PAAS-BOSS-DB1.webcache > 192.168.11.251.4507: Flags [.], ack 2, win 54, length 0
09:48:56.191594 IP 192.168.11.251.4503 > PAAS-BOSS-DB1.webcache: Flags [F.], seq 1, ack 1, win 64240, length 0
09:48:56.191602 IP PAAS-BOSS-DB1.webcache > 192.168.11.251.4503: Flags [.], ack 2, win 88, length 0
09:48:57.935215 IP PAAS-BOSS-DB1.webcache > 192.168.11.251.ipsec-nat-t: Flags [F.], seq 3367166939, ack 591490835, win 105, length 0
09:48:57.935994 IP 192.168.11.251.ipsec-nat-t > PAAS-BOSS-DB1.webcache: Flags [.], ack 1, win 64021, length 0
09:48:57.936401 IP 192.168.11.251.ipsec-nat-t > PAAS-BOSS-DB1.webcache: Flags [F.], seq 1, ack 1, win 64021, length 0
09:48:57.936413 IP PAAS-BOSS-DB1.webcache > 192.168.11.251.ipsec-nat-t: Flags [.], ack 2, win 105, length 0
09:48:58.667198 IP PAAS-BOSS-DB1.webcache > 192.168.11.251.4502: Flags [F.], seq 3367552596, ack 2873947055, win 71, length 0
09:48:58.667906 IP 192.168.11.251.4502 > PAAS-BOSS-DB1.webcache: Flags [.], ack 1, win 64240, length 0
09:48:58.668218 IP 192.168.11.251.4502 > PAAS-BOSS-DB1.webcache: Flags [F.], seq 1, ack 1, win 64240, length 0
09:48:58.668231 IP PAAS-BOSS-DB1.webcache > 192.168.11.251.4502: Flags [.], ack 2, win 71, length 0
另外 我們還可以把linux下面抓包的內容 拿到鯊魚里面進行分析
./tcpdump -w tcp.out tcp port 5222
然后下載tcp.out 文件,到鯊魚里面進行分析
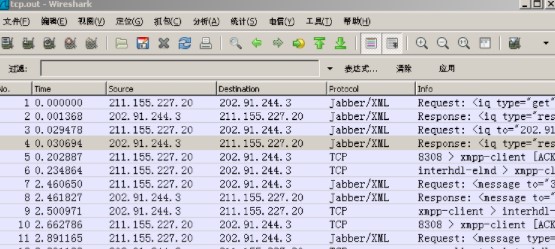
大家若想了解更多相關知識,不妨來關注一下動力節(jié)點的Java開發(fā)工具,里面有更多的工具介紹供大家學習,希望對大家能夠有所幫助。